Headers Settings
This reference covers all of Pomerium's Headers Settings:
- Host Header Settings
- Set Request Headers
- Remove Request Headers
- Set Response Headers
- Rewrite Response Headers
Host Header Settings
By default, Pomerium will set the Host header of an upstream request according to the host specified in the To URL for the route.
(Strictly speaking, the Host header is used only with HTTP/1.1. For HTTP/2 and HTTP/3 the :authority pseudo-header is used instead. These settings affect both identically.)
You can change how Pomerium sets this header using the following settings:
1. Preserve Host Header
preserve_host_header passes the Host header from the incoming request to the upstream service, instead of the host from the route's To URL.
This is like the Apache httpd ProxyPreserveHost directive.
2. Host Rewrite
host_rewrite rewrites the Host header to a fixed value.
3. Host Rewrite Header
host_rewrite_header rewrites the Host header using the value of some other header from the incoming request. For example:
host_rewrite_header: X-My-Host
For an incoming request with the header X-My-Host: foo.example.com, this would rewrite the Host header to foo.example.com.
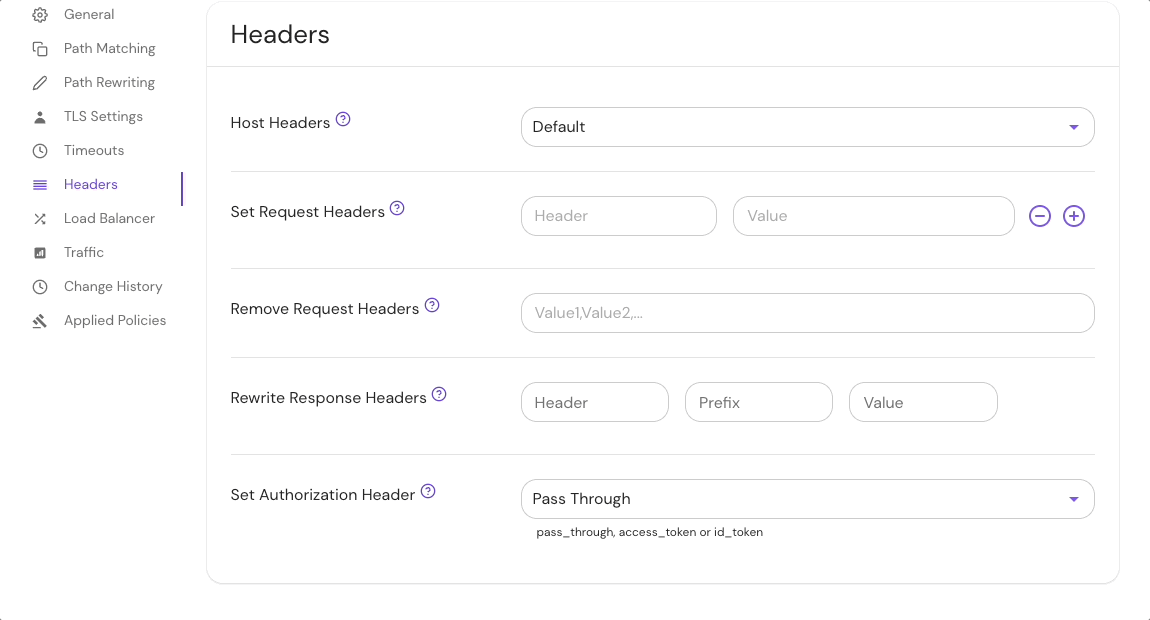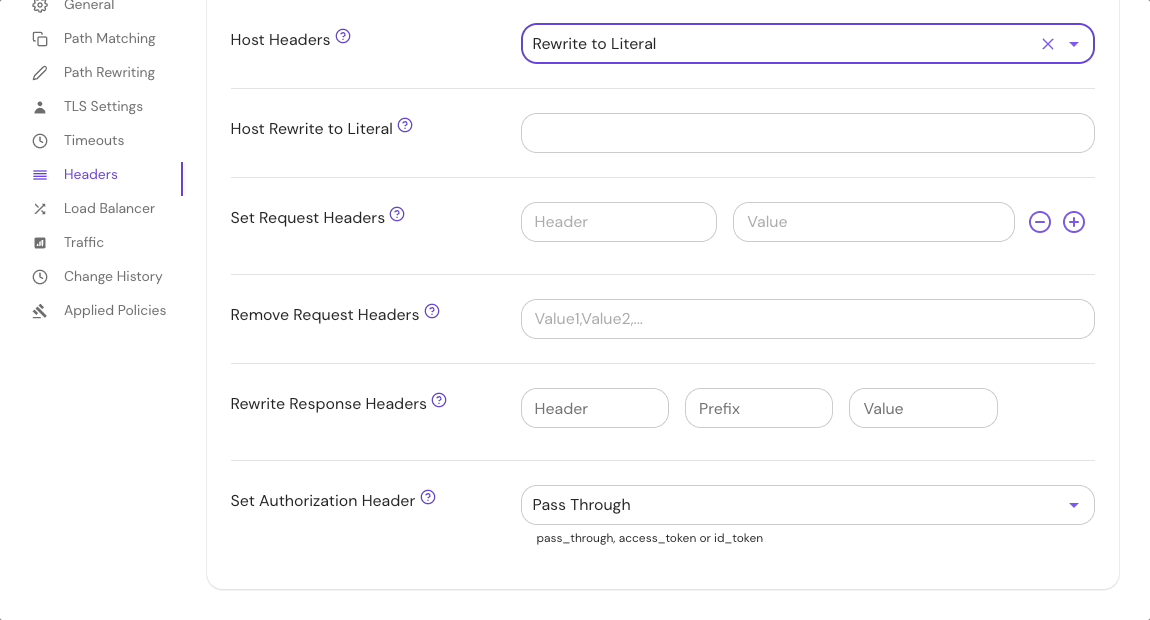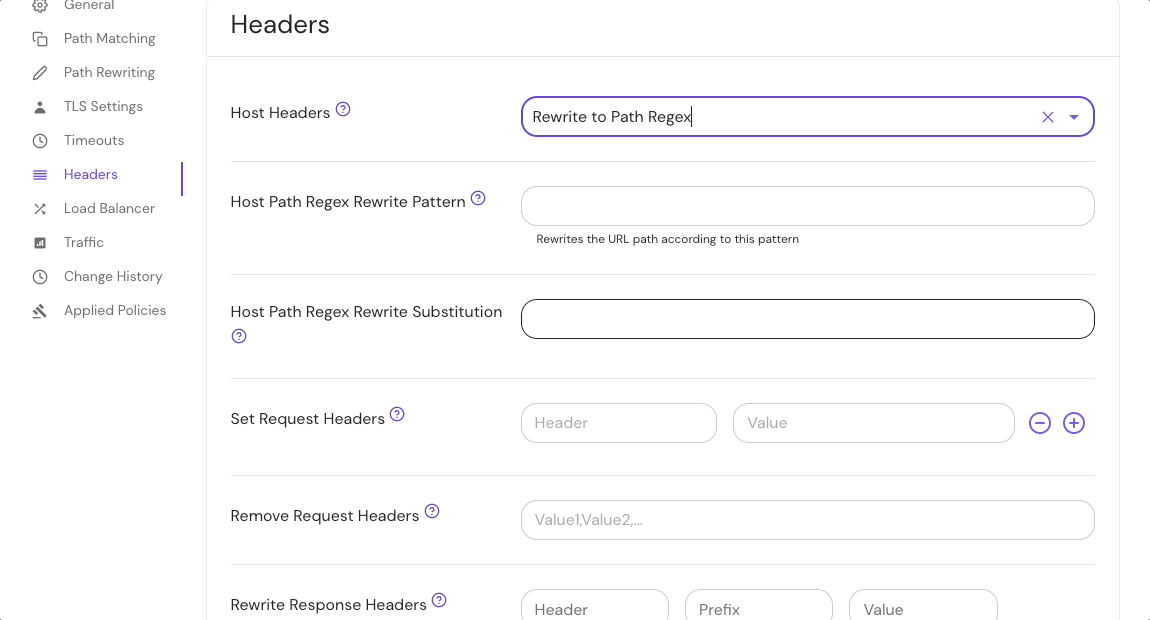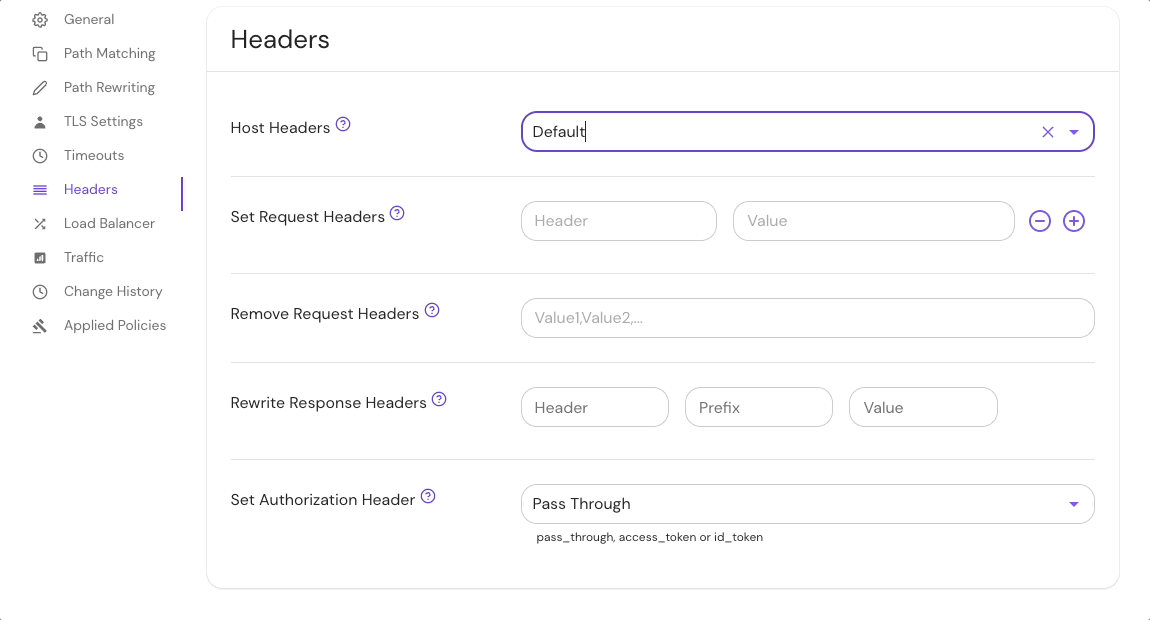
4. Host Path Regex Rewrite Pattern/Substitution
host_path_regex_rewrite_pattern and host_path_regex_rewrite_substitution rewrite the Host header based on a regular expression substitution using the URL path as the input. For example:
host_path_regex_rewrite_pattern: '^/(.+)/.+$'
host_path_regex_rewrite_substitution: \1
For a request URL with the path /example.com/some/path, this would rewrite the Host header to example.com.
How to Configure
- Core
- Enterprise
- Kubernetes
| YAML/JSON settings | Type | Usage |
|---|---|---|
preserve_host_header | boolean | optional |
host_rewrite | string | optional |
host_rewrite_header | string | optional |
host_path_regex_rewrite_pattern | string | optional |
host_path_regex_rewrite_substitution | string | optional |
Examples
preserve_host_header: true
host_rewrite: 'example.com'
Configure Host Header settings in the route Headers settings in the Console:
| Annotation name | Type | Usage |
|---|---|---|
host_rewrite | string | optional |
Examples
ingress.pomerium.io/host_rewrite: 'example.com'
Set Request Headers
Set Request Headers allows you to set both static and dynamic values for given request headers. Static values can be useful if you want to pass along additional information to upstream applications as headers, or to set a fixed authentication header on the request.
The dynamic values enable you to pass ID and Access tokens from your identity provider to upstream applications.
To pass dynamic values from the user's OIDC claim to an upstream service, see JWT Claim Headers.
Neither HTTP/2 pseudo-headers (for example, :authority) nor the Host header may be modified via this mechanism. The request path may instead be modified using the Path Rewriting Settings and the Host header may be modified using the Host Header Settings above.
How to Configure
- Core
- Enterprise
- Kubernetes
| YAML/JSON setting | Type | Usage |
|---|---|---|
set_request_headers | map of key-value pairs | optional |
Examples
Pass static header values in the request:
- from: https://verify.corp.example.com
to: https://verify.pomerium.com
policy:
- allow:
or:
- email:
is: user@example.com
set_request_headers:
# Set a fixed Basic Auth username and password (root:hunter42)
Authorization: Basic cm9vdDpodW50ZXI0Mg==
# Set a custom header
X-Your-favorite-authenticating-Proxy: 'Pomerium'
# To include a '$' character in a header value:
X-Hello: $$world # header value is set to "$world"
Pass ID token, access token, and client certificate fingerprint (if present) as dynamic headers in the request:
- from: https://verify.corp.example.com
to: https://verify.pomerium.com
policy:
- allow:
or:
- email:
is: user@example.com
set_request_headers:
x-pomerium-idp-id-token: ${pomerium.id_token}
x-pomerium-idp-access-token: ${pomerium.access_token}
x-pomerium-client-cert-fingerprint: ${pomerium.client_cert_fingerprint}
Configure Set Request Headers in the Console:
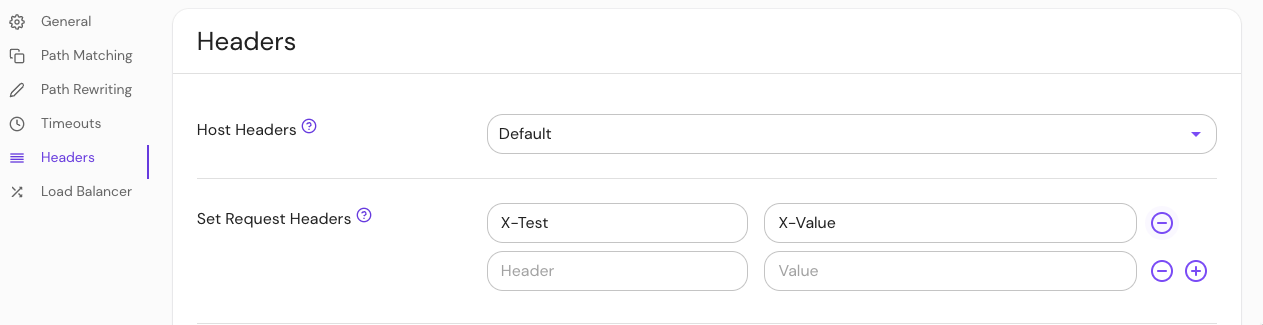
| Annotation name | Type | Usage |
|---|---|---|
set_request_headers | map of key-value pairs | optional |
ingress.pomerium.io/set_request_headers: |
X-Test: X-Value
Pass Dynamic Tokens in Headers
The following token substitutions are available:
| Token | Value |
|---|---|
${pomerium.access_token} | OAuth access token from the identity provider* |
${pomerium.client_cert_fingerprint} | Short form SHA-256 fingerprint of the presented client certificate (if downstream mTLS is enabled) |
${pomerium.id_token} | OIDC ID token from the identity provider* |
${pomerium.jwt} | Pomerium JWT (this is the same value as in the X-Pomerium-Jwt-Assertion header) |
*The ID token and access token are not available when using the Hosted Authenticate service.
Note: Token values must use the ${pomerium.<token>} syntax. To include a literal $ character in a header value, use $$.
Be very careful when passing access tokens to an upstream application. This may allow the application to make other authenticated requests on behalf of the user.
Rewrite Request Headers
In addition to token substitutions, request headers can be rewritten using ${pomerium.request.headers["HEADER-NAME"]}. For example if a request had a header X-Jwt: JWT and you would like to send it as Authorization: Bearer JWT, you could do so using:
set_request_headers:
Authorization: Bearer ${pomerium.request.headers["X-Jwt"]}
Remove Request Headers
Remove Request Headers allows you to remove given request headers. This can be useful if you want to prevent privacy information from being passed to downstream applications.
How to Configure
- Core
- Enterprise
- Kubernetes
| YAML/JSON setting | Type | Usage |
|---|---|---|
remove_request_headers | string | optional |
Examples
- from: https://verify.corp.example.com
to: https://verify.pomerium.com
policy:
- allow:
or:
- email:
is: user@example.com
remove_request_headers:
- X-Email
- X-Username
Set Remove Request Headers in the Console:
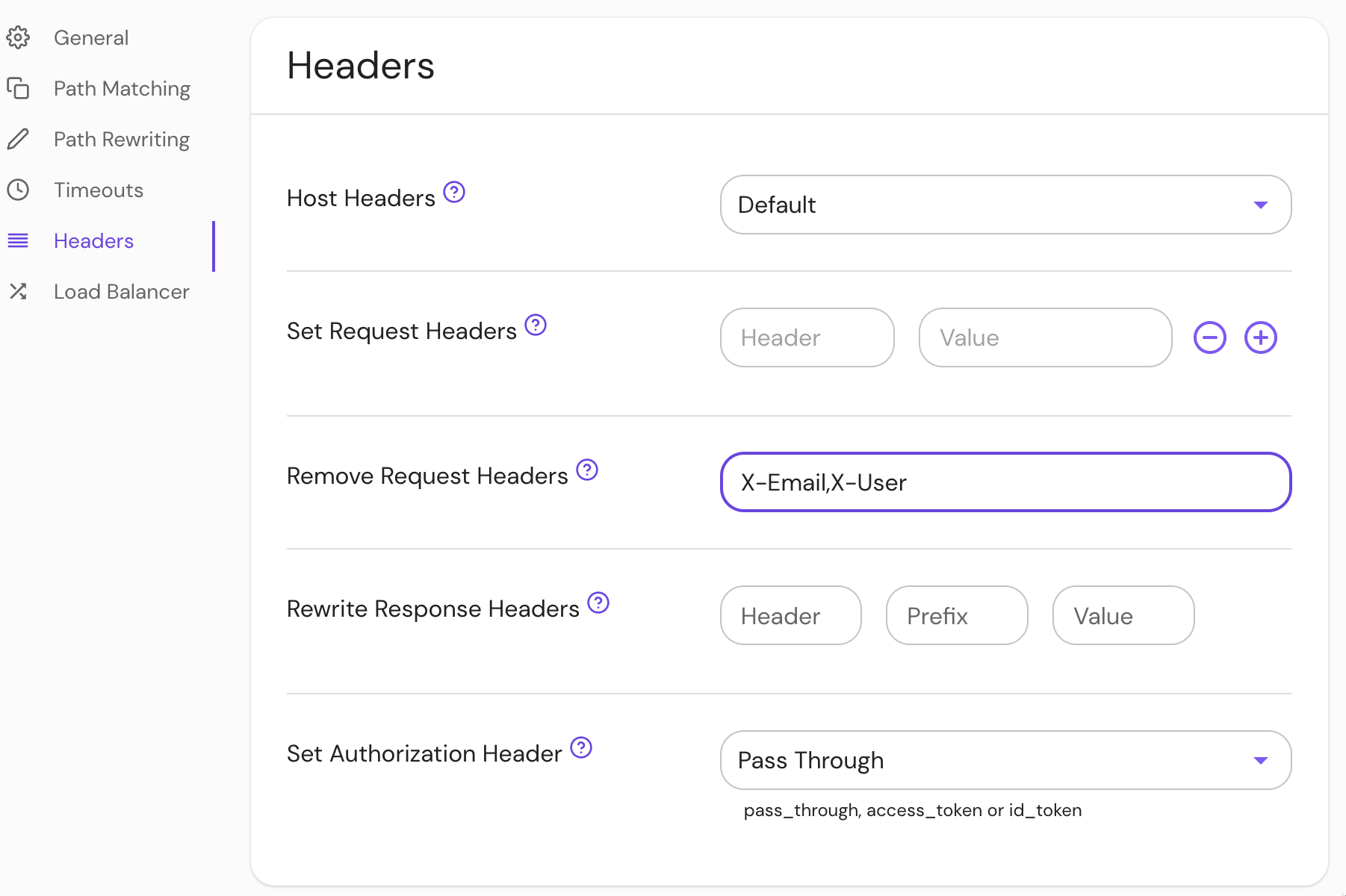
| Annotation name | Type | Usage |
|---|---|---|
remove_request_headers | string | optional |
ingress.pomerium.io/remove_request_headers: |
- X-Email
- X-User
Set Response Headers
Set Response Headers allows you to set static values for the given response headers. These headers will take precedence over the global set_response_headers.
How to Configure
- Core
- Enterprise
- Kubernetes
| YAML/JSON setting | Type | Usage |
|---|---|---|
set_response_headers | string | optional |
Examples
set_response_headers:
X-Test: X-Value
Configure Set Response Headers in the Console:
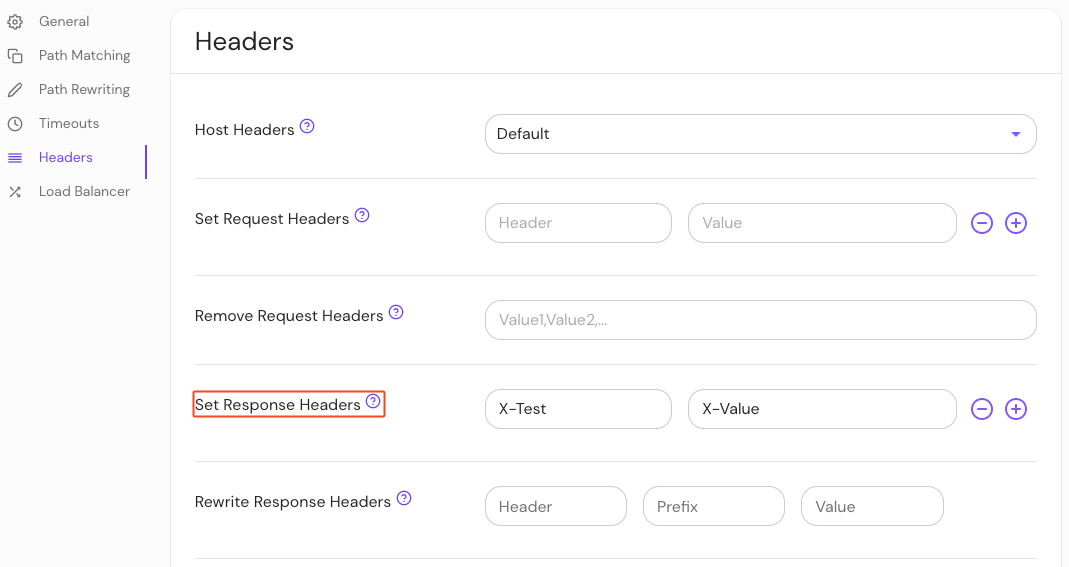
| Annotation name | Type | Usage |
|---|---|---|
set_response_headers | string | optional |
ingress.pomerium.io/set_response_headers: |
X-Test: X-Value
Rewrite Response Headers
Rewrite Response Headers allows you to modify response headers before they are returned to the client. The header field will match the HTTP header name, and prefix will be replaced with value.
How to Configure
- Core
- Enterprise
- Kubernetes
| YAML/JSON setting | Type | Usage |
|---|---|---|
rewrite_response_headers | object | optional |
Examples
If the downstream server returns a header:
Location: http://localhost:8000/two/some/path/
And the policy has this config:
rewrite_response_headers:
- header: Location
prefix: http://localhost:8000/two/
value: http://frontend/one/
The browser would be redirected to: http://frontend/one/some/path/. This is similar to nginx's proxy_redirect option, but can be used for any header.
Configure Rewrite Response Headers in the Console:
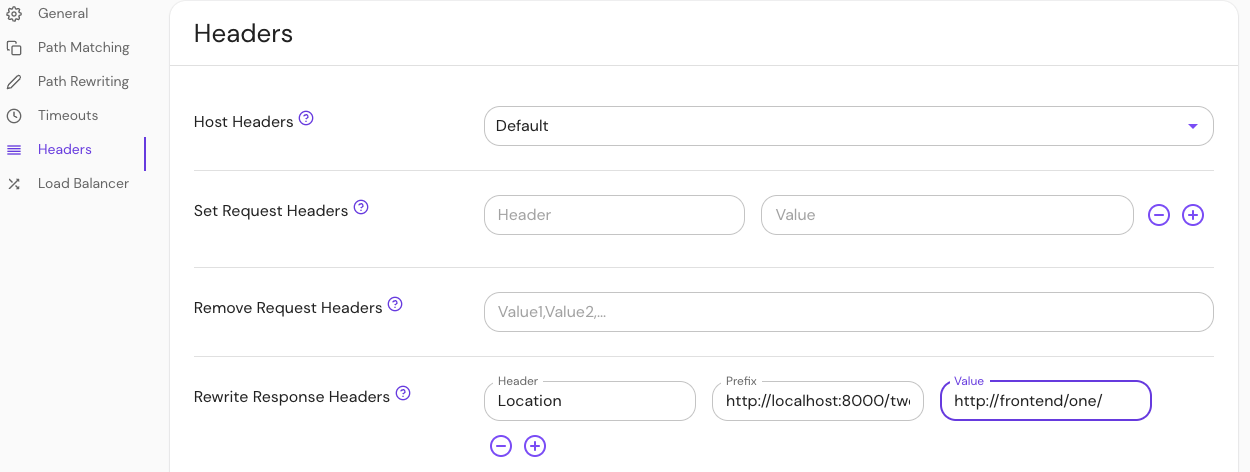
| Annotation name | Type | Usage |
|---|---|---|
rewrite_response_headers | object | optional |
Examples
If the downstream server returns a header:
Location: http://localhost:8000/two/some/path/
And the Ingress object has this annotation:
ingress.pomerium.io/rewrite_response_headers: |
- header: Location
prefix: http://localhost:8000/two/
value: http://frontend/one/
The browser would be redirected to: http://frontend/one/some/path/. This is similar to nginx's proxy_redirect option, but can be used for any header.